This article is aimed at individuals interested in or involved with cryptocurrency investments and transactions. It’s designed to educate both beginners and those with some crypto experience about common types of crypto attacks, enabling them to recognize and protect themselves from potential threats. The content provides valuable insights for anyone looking to navigate the crypto landscape safely and make informed decisions about their digital assets.
Introduction: Navigating the Threat Landscape
The allure of cryptocurrencies has not only attracted legitimate investors but also opportunistic cybercriminals. As the crypto market gains momentum, the risk of falling prey to malicious activities grows. To empower yourself against these threats, it’s crucial to understand the common types of crypto attacks that could compromise your digital assets. By arming yourself with knowledge, you can navigate this evolving landscape with confidence and protect your investments.
1. Unveiling Cryptojacking: Covert Mining for Illicit Gains
Crypto mining has established itself as a profitable industry, with millions of miners globally seeking to secure blockchain networks and earn rewards. However, the allure of financial gain has not escaped the notice of malicious actors. This has given rise to the phenomenon known as cryptojacking—a stealthy cybercrime that exploits the resources of unwitting victims for personal gain. By unauthorizedly harnessing victims’ mining hardware, cybercriminals circumvent the need for specialized equipment and expend minimal computing power. This form of attack often goes unnoticed, making detection a challenge.
Protecting yourself from cryptojacking requires heightened awareness and proactive measures. Employing robust antivirus software across all your devices can serve as an essential defense against cryptojacking malware. By prioritizing your cybersecurity, you not only thwart cryptojackers but also fortify your protection against a broader spectrum of threats.

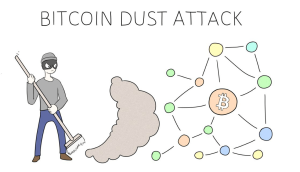
2. Dust Attacks: Uncovering Privacy Vulnerabilities
Within the intricate world of cryptocurrencies, the term “dust” has taken on a new connotation—one that malicious actors exploit for their benefit. Dust attacks involve sending negligible amounts of leftover crypto after transactions. While these amounts may seem inconsequential, they can serve as a gateway for privacy invasion. Attackers conduct dust transactions across multiple wallet addresses, allowing them to trace and potentially expose the identities of targeted wallet holders.
The impact of dust attacks extends beyond financial loss. Attackers armed with even a fraction of your information can launch more sophisticated attacks like phishing scams. To shield yourself from this menace, a heightened sense of vigilance is crucial. Utilizing wallets that offer enhanced privacy features, along with regularly monitoring and consolidating your funds, can help mitigate the risks associated with dust attacks.
3. Safeguarding Your Private Key: A Critical Defense Mechanism
In the realm of cryptocurrency management, the private key stands as a vital linchpin in securing your digital assets. This alphanumeric code empowers you to authorize transactions and access your holdings. The potential for private key theft looms ominously, and a compromised private key could spell disaster for your investments.
To bolster your defense against private key theft, meticulous wallet selection is essential. Opt for reputable wallets that prioritize security, and consider the nuances between software and hardware options. Hardware wallets, which provide an additional layer of physical security, are generally favored for safeguarding private keys. Strengthening your protection further involves incorporating multiple security layers, including PINs, backup seed phrases, biometric logins, and timed lockouts.

Conclusion: Fortifying Your Crypto Journey
In a landscape where digital assets are susceptible to sophisticated threats, vigilance and knowledge become paramount. As you traverse the world of cryptocurrencies, equip yourself with insights into prevalent crypto attacks and their countermeasures. By adopting stringent security practices and opting for reputable wallets, you fortify your crypto journey, ensuring that your investments remain out of reach for malicious actors. Empowerment through awareness paves the way for a safer and more secure digital financial future.