This article aims to educate readers about the potential security risks posed by malicious Chrome extensions and how they can impact businesses, helping them understand the importance of cautious extension usage to ensure the safety of their network and data.
Understanding Chrome Web Store Safety
Google’s Chrome Web Store is a widely used platform for downloading browser extensions. It comes with its own set of safety measures to prevent the distribution of malware-infested extensions. While Google endeavors to maintain a secure environment, the reality is that no system is completely impervious to threats. Despite the Web Store’s rigorous approval process and monitoring mechanisms, some malicious extensions can still evade detection, creating opportunities for exploiting vulnerabilities.
A New Breed of Threat: Business Network Attacks
In recent times, a concerning trend has emerged—malicious Chrome extensions that target business networks. Unlike traditional malware that confines its effects to a single PC, this new breed of threat aims to infiltrate an organization’s network. Once established, hackers can delve deeper into the network, potentially gaining access to sensitive data and compromising the security of the entire infrastructure. This represents an unprecedented level of risk, requiring businesses to adopt heightened security measures.
Real-Life Cases: Malware in Action
Evidence of this growing threat comes from instances where malicious Chrome extensions have successfully breached business networks. In one such case, 106 extensions with malicious intent were identified and reported to Google for removal. What was particularly alarming was not just the data theft; these extensions created a backdoor entry point, enabling hackers to breach the network further. This highlighted the potential for widespread infiltration and data compromise within organizations.
Mechanisms Behind the Threat
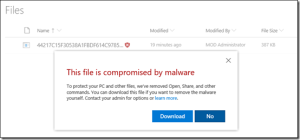
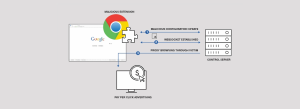
The sophisticated methods employed by malware developers to evade security checks reveal the adaptability and resourcefulness of cybercriminals. These malicious extensions often redirect victims to seemingly harmless websites to download infected files. However, their true genius lies in the creation of “morphing websites” that trick security systems. By detecting the source of the connection, these websites present legitimate content to fool virus checkers. This allows the malware payload to be effectively concealed.
Extent of Damage: A Wide Reach
The potency of these malicious extensions is evident from the scale of their impact. The 32 million downloads of these seemingly benign extensions underscore the vast reach of these malware campaigns. Affected sectors span across industries, including finance, healthcare, and government organizations. This comprehensive infiltration signifies a calculated effort by cybercriminals to establish footholds in multiple sectors simultaneously.
Identifying and Defending Against Malicious Extensions
To safeguard against these threats, businesses and individuals must exercise due diligence. Carefully vetting extensions before installation is paramount. Limiting the number of extensions used to essential and reputable ones can significantly mitigate risks. Regularly reviewing and deleting unused extensions can also minimize potential vulnerabilities. Furthermore, relying on extensions directly from trusted sources like the Chrome Web Store can enhance security.
Trusted Extensions: Your Shield Against Malware
In a landscape where trust is paramount, selecting extensions from established publishers with positive reviews becomes crucial. These extensions have a track record of security and reliability, reducing the likelihood of encountering malware. It’s important to prioritize security over convenience, ensuring that each extension added to your browser is thoroughly examined for potential risks.
Conclusion
The emergence of malicious Chrome extensions targeting business networks serves as a stark reminder of the evolving nature of cybersecurity threats. While browser extensions can undoubtedly enhance productivity, the potential risks associated with these tools must not be underestimated. By staying vigilant, conducting thorough research, and adopting a cautious approach to extension installation, businesses can fortify their networks against these emerging threats. In the ever-changing landscape of digital security, knowledge and proactive measures remain the best defense against malicious actors seeking to exploit vulnerabilities.




