Introduction to Cloud Workload Protection Platforms (CWPPs)
In the ever-evolving landscape of cloud computing, ensuring the security of your data and workloads is paramount. The shift from conventional on-premises servers to cloud-based environments has ushered in a new era of flexibility and efficiency. However, with this transition comes the critical task of safeguarding sensitive information, which can be more challenging in cloud environments due to their dynamic nature.
This is where Cloud Workload Protection Platforms (CWPPs) come into play. CWPP technology serves as a digital guardian for your cloud workloads, offering a robust defense against threats and ensuring data protection. In this article, we delve into the world of CWPPs, exploring their significance in the realm of cloud security.
Understanding Cloud Workloads
Before delving into the specifics of CWPPs, it’s essential to grasp the concept of cloud workloads. Cloud workloads encompass a wide array of computing tasks and services within cloud-based resources. These workloads can include microservices, Hadoop nodes, databases, Infrastructure as a Service (IaaS), containers, and Virtual Machines (VMs).
The dynamic and diverse nature of cloud workloads presents unique security challenges. Unlike traditional on-premises servers, cloud workloads traverse various environments, making them susceptible to threats. This is where CWPPs step in to provide comprehensive security solutions tailored to the workload-centric nature of the cloud.
The Role of CWPPs in Workload Protection
CWPPs are designed to define, implement, and monitor centralized security measures for cloud workloads, regardless of their location, form, or lifecycle. These platforms are dedicated to safeguarding workloads as they move between cloud and hybrid environments, preventing data leaks and unauthorized infiltrations.
To protect cloud workloads effectively, CWPPs employ various strategies. They create network segmentation through firewalls to enhance traffic monitoring and visibility, enabling robust log management. Additionally, CWPPs offer workload vulnerability management, monitoring behavioral patterns, and conducting anti-malware scanning, akin to Endpoint Detection and Response (EDR) and Host-based Intrusion Detection Systems (HIDS).
In essence, CWPPs can be likened to antivirus and optimization software tailored specifically for cloud workloads.
Key Benefits of CWPPs
Implementing CWPP technology brings several key advantages to cloud security:
- Enhanced Security: CWPPs provide an additional layer of security against targeted attacks, complementing the security protocols of cloud vendors.
- Cloud Visibility: These platforms offer comprehensive cloud visibility, facilitating faster threat detection and response.
- Cloud and Human Performance Optimization: CWPPs enable cloud optimization by collecting analytics from applications, resulting in improved performance. Moreover, they centralize all cloud workloads, reducing the need for manual updates, scans, and reports, thus optimizing human performance.
- Cost Reduction: Fewer personnel are required to manage security, leading to reduced operational and hardware costs.
Leading Companies Offering CWPP Solutions
Several renowned security software development companies offer CWPP solutions. Some of the notable names in this domain include:
- McAfee Server Security Suite
- Symantec Cloud Workload Protection
- Microsoft Defender for Cloud
- Sysdig Secure DevOps Platform
- Trend Micro Deep Security
Complementary Cloud Security Tools
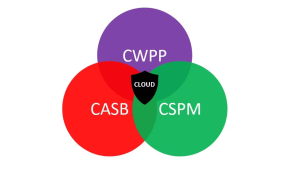
CWPPs often work in conjunction with other cloud security tools, such as Cloud Security Posture Management (CSPM) and Cloud Access Security Broker (CASB). While these tools may have overlapping features, each specializes in a specific aspect of cloud security.
- CSPM focuses on compliance with cloud security configurations and implementing security and compliance processes.
- CASB ensures that network traffic complies with an organization’s security policies before granting access to the network.
The synergy between CWPPs, CSPM, and CASB enhances the optimization and security of cloud workloads and data.
The Necessity of CWPP Technology
In today’s era of evolving cyber threats and data breaches, the protection of cloud workloads is a top priority. CWPPs enable organizations to implement robust security measures across diverse cloud environments, reducing complexity, and enhancing portability.
No other software solution offers the level of protection and centralized control provided by CWPPs. Therefore, CWPP technology is indispensable for safeguarding against cyber threats and ensuring the integrity and security of cloud workloads and data in an ever-changing digital landscape.
Table: Key Features of Cloud Workload Protection Platforms (CWPPs)
| Feature | Description |
|---|---|
| Workload-Centric Security | Provides centralized security measures tailored for cloud workloads, ensuring comprehensive protection. |
| Network Segmentation | Creates network segmentation through firewalls for enhanced traffic monitoring and log management. |
| Workload Vulnerability Management | Monitors behavioral patterns, conducts anti-malware scanning, and offers Endpoint Detection and Response (EDR) capabilities. |
| Cloud Visibility | Facilitates comprehensive visibility into cloud environments, enabling faster threat detection and response. |
| Cloud and Human Performance Optimization | Collects analytics for cloud optimization, reducing the need for manual updates and scans. |
| Cost Reduction | Decreases operational and hardware costs by minimizing the requirement for security personnel. |
Conclusion: Strengthening Cloud Security with CWPPs
As organizations increasingly embrace cloud computing and dynamic workloads, ensuring the security of sensitive data becomes paramount. Cloud Workload Protection Platforms (CWPPs) emerge as essential guardians, providing comprehensive security solutions tailored for cloud workloads.
CWPPs play a pivotal role in protecting diverse cloud workloads, ranging from microservices to databases and virtual machines. They offer workload-centric security, implementing network segmentation through firewalls and vulnerability management to monitor behavior and prevent malware intrusions. Furthermore, CWPPs enhance cloud visibility, enabling faster threat detection and response.




