This content is designed for business owners, IT professionals, and cybersecurity enthusiasts seeking a comprehensive understanding of Zero Trust Networks (ZTNs) and their benefits. Readers will gain insights into the limitations of traditional VPNs and the advantages offered by ZTNs with Software-Defined Perimeters (SDPs). The article aims to empower the audience with knowledge to make informed decisions about enhancing their organization’s cybersecurity.
Evolving Beyond VPNs: The Need for a Safer Approach
In a digital landscape rife with cyber threats, Virtual Private Networks (VPNs) have stood as stalwart defenders of online privacy. Yet, as the cybercriminal arsenal evolves, vulnerabilities in the traditional VPN model have become apparent. The year 2020 witnessed over 1000 hacked VPN servers, laying bare the risks associated with legacy solutions. This underscores the urgency for businesses to explore alternatives that offer superior functionality and security. Enter Zero Trust Networks (ZTNs), a paradigm that promises to revolutionize data protection and redefine the way organizations safeguard their sensitive information.
Zero Trust Networks: Reinventing Cybersecurity
Zero Trust Networks (ZTNs) stand as a beacon of innovation in an era where the conventional concept of a trusted user has lost its sheen. At its core, ZTNs discard the notion of inherent trust and prioritize stringent user authentication. The organization rigorously scrutinizes every incoming user request and grants access based on necessity rather than a blanket allowance. This user-centric approach ensures that the organization shields the heart of its data—the central repository—from compromise, even if the credentials of a remote user fall into the wrong hands. This departure from the past marks a turning point in cybersecurity strategies.
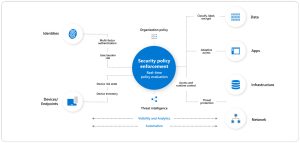
Software-Defined Perimeters: The Pillars of ZTNAs
Central to the implementation of Zero Trust Network Access (ZTNA) models are Software-Defined Perimeters (SDPs). SDPs introduce a dynamic layer of security that transcends traditional VPN models. These perimeters establish secure connections while obscuring data, ensuring that every user is confined within their designated bubble of access. The allure lies in the ability of SDPs to recognize patterns in user behavior, sounding the alarm when anomalous actions occur. This proactive stance enhances the security posture by promptly identifying and responding to potential breaches.
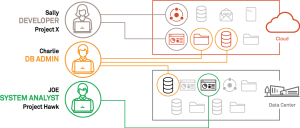
Advantages of Zero Trust Networks and Implementing SDPs
The migration toward cloud-based operations underscores the inadequacies of legacy security solutions. Zero Trust Networks (ZTNs) rise to the occasion by embracing multi-dimensional security standards. The Software-Defined Perimeter (SDP) architecture is a testament to this, ensuring that confidential resources are accessed via secure remote connections. Unlike VPNs, which often permit broad access, SDPs grant users access only to what they need—minimizing exposure and reducing attack vectors. The real-time monitoring feature of ZTNAs further bolsters their defenses, detecting breaches in their infancy.

Conclusion: Fortifying the Digital Realm
As the hack of Pulse Secure’s VPN servers serves as a sobering reminder of the evolving threat landscape, the importance of proactive cybersecurity measures has never been clearer. Zero Trust Networks (ZTNs) stand as a formidable alternative to traditional VPNs, boasting multi-layered security, user-centricity, and real-time monitoring. The paradigm shift towards Software-Defined Perimeters (SDPs) within ZTNAs further enhances security. While Small-scale enterprises might still find value in VPNs, ZTNAs offer an advanced approach for modern businesses. In an age where digital assets hold unparalleled value, the journey toward enhanced data protection is a necessary evolution.